You Want to Know What Protocols Are Being Used on Your Network
Identify network hardware and protocols
1 Layered network protocols
- Network communication relies upon the interaction of many different protocols. These protocols are designed to implement a detail set of rules and conventions governing particular aspects of how devices in a network communicate.
- Network protocols are arranged in layers, with each layer providing a specialised service for the layer higher up. Because each layer consists of standardised protocols that perform functions to an agreed gear up of rules, it is possible to change individual protocols within a layer without having to modify protocols in other layers.
- To visualise this concept of layers, consider a conversation betwixt two people:
- Content layer: ideas exchanged in chat.
- Rules: hold to speak a mutual language, take turns speaking, not to interrupt when others are speaking.
- Physical: face-to-face communication requires speakers to be close enough to hear each other.
- In this example, the conversation has been divided into three layers. The physical layer considers the fundamental requirements of exchanging information between two people using speech. This includes considering the distance between the speakers, which will affect how loud each person needs to talk in order for the other to hear. Spoken communication is a motility of air, which is translated as audio waves. This means that the conversation could have place in a 'nigh' vacuum like outer space.
- The rules layer defines how the speakers volition talk. To exchange information, a common linguistic communication would demand to exist called. Once the language is agreed, how is the chat to be managed? Taking turns is a reasonable way to converse with another person and interrupting would be considered rude. But what happens if 1 person misses something and wishes it to exist repeated? Do they ask for information technology to be repeated verbally, or do they use an agreed signal such as raising a mitt?
- The content layer considers the actual message exchanged betwixt the 2 speakers, which in a conversation may be an item of news, plans for a vacation or just gossip.
- By dividing the conversation into layers, we have decided upon the particular functions that are required by each layer to support communication, and in our elementary layered model, it should be possible to alter some aspects within ane layer without affecting the others. For example, if we at present decide to have a phone conversation, how does this alter the requirements of our physical layer?
- Networking protocols can exist layered in a similar manner to the vocalism conversation in the example above, but has a wider range of considerations and uses unlike terms:
- Encoding: language to apply.
- Formatting: greeting, recipient identity, endmost phrase, sender identity.
- Message size: segmentation of data.
- Timing: menstruation command and timeout.
- Delivery: to one host (unicast), to all hosts (broadcast), to some hosts (multicast).
2 TCP/IP reference model
- The protocols used within the Internet were designed using a layered model referred to as the TCP/IP reference model:
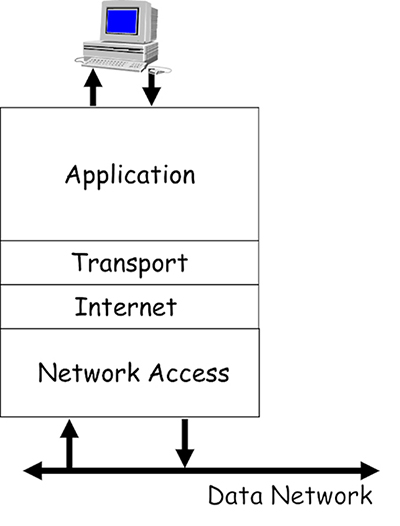
- These protocols operate on your calculating devices, and allow the programs y'all use to access the data network via the single network interface carte (NIC) that is fitted to virtually devices. Imagine how difficult this chore would be for your device if you lot used multiple programs that required network admission – for case, surfing the Www (Www), downloading a file and sending an electronic mail.
- All these different programs expect to be able to simultaneously access your NIC in gild to transport and receive information. The purpose of the TCP/IP reference model is to allow the design and cosmos of protocols that can support the network requirements of various installed programs competing for the attending of a single NIC.
- Each layer of the model defines the function of the protocols that operate within it:
- Application: provides the interface between the other layers and the operating system software on your computing device.
- Transport: manages application layer data and prepares information technology for manual by segmenting it into easily manageable blocks. It is likewise responsible for allowing multiple programs to simultaneously access the NIC, and managing the reliable commitment of data if required.
- Internet: manages the delivery of data encapsulated in packets beyond networks.
- Network access: manages the delivery of data across local network media, regardless of the concrete media type.
- Groups of protocols that are created in accordance with a protocol model are referred to every bit a protocol suite. The TCP/IP protocol suite operates in accordance with the TCP/IP reference model, and it is the predominant suite used within the Internet.
v Internet layer
- This layer allows calculating devices to commutation data across networks. It receives segments of data from the transport layer protocols and encapsulates them within packets. The packets comprise address information identifying the source and destination devices, allowing parcel switching devices such as routers to route them to the right destination network.
- There are two Internet layer protocols currently in apply:
- Net Protocol v4 (IPv4): this is the well-nigh pop TCP/IP Internet layer protocol, which uses 32-scrap addresses, superseding historically previous versions. The networking industry is slowly phasing out IPv4 due to the rapid growth of the Net and the increasing demand for IP addresses, which it tin can no longer support. Still, this will take considerable time as in that location are many systems and devices nonetheless defended to IPv4.
- Internet Protocol v6 (IPv6): this is the replacement for IPv4. It uses a 128-chip address and is capable of supporting the expected future growth of devices connecting to the Internet.
- The switchover from IPv4 to IPv6 was facilitated past the layered approach to network protocols. Because IPv6 can perform the aforementioned function every bit IPv4, there was no requirement to redesign the protocols higher up (TCP and UDP) or below the Internet layer.
Activity: Compare IPv4 to IPv6
By signing in and enrolling on this form you can view and complete all activities within the course, track your progress in My OpenLearn Create. and when yous have completed a course, you can download and impress a free Statement of Participation - which you tin apply to demonstrate your learning.
7.2.1 Switches
- Switches provide connectivity points within a network, allowing you to add a big number of devices to a network, typically using UTP cabling. Because the most mutual network access protocol is Ethernet, most switches will support it and are thus referred to as Ethernet switches. Ethernet switches have now largely replaced the older and much slower Ethernet hubs.

- Switches provide multiple Ethernet NICs, which are referred to as ports. You can use a UTP cable to connect multiple computing devices to the ports:
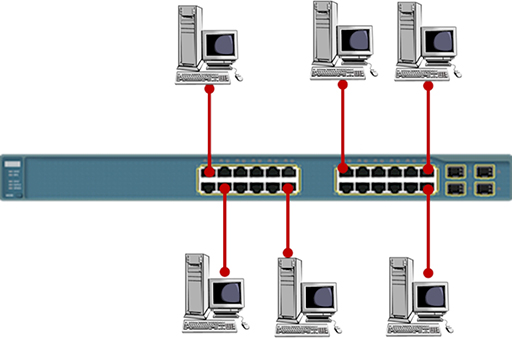
- The term used to describe the layout of your devices is 'network topology'. The elementary layout shown higher up is referred to equally a star topology, as it resembles a multi-pointed star. Note that each of the UTP cables shown must be no longer than 100m.
- The number of computing devices you tin connect using a single switch is limited to the number of ports that are available. If you need to add more devices, or you wish to extend the size of your network, you can connect two switches together. This topology is referred to as an extended star:
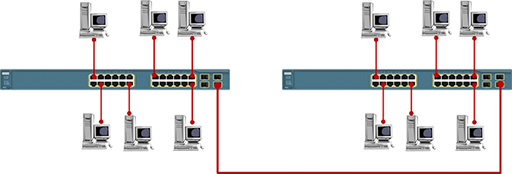
- The Ethernet network access protocol was originally designed to back up data rates of 10Mbps. This is too slow to support modernistic networks, so the protocol has evolved to support greater information rates.
- Most Ethernet switches are capable of supporting several Ethernet variants on each port. Although it is possible to configure each port to operate at a detail information charge per unit, most Ethernet switches volition negotiate with the connected computing device and set themselves to the highest information rate that they both support. It is all-time practice to connect switches together using the fastest data rate port available.
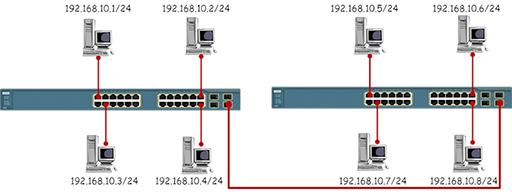
- Switches forwards information between computers using the destination MAC addresses contained in the frames they receive. This means that switches have no knowledge of the IP addresses of the packets contained within the frames, so they cannot be used to bring together together different IP networks. Referring to the diagram below, all the PCs are addressed within the same IP network and the switches will successfully frontwards data between them.
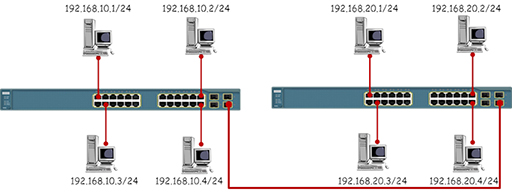
- The diagram beneath shows the same topology, but this time the PCs have been placed in dissimilar IP networks. While the switches will forward information between the PCs based on the MAC addresses in the Ethernet frames, the PCs will reject to communicate with devices exterior their ain IP network.
Activity: Information rates
Research the information rates supported by the following Ethernet variants:
| Protocol | Data rate |
|---|---|
| Ethernet | 10Mbps |
| Fast Ethernet | |
| Gigabit Ethernet | |
| ten Gigabit Ethernet |
Interactive feature not available in single page view (see it in standard view).
seven.two.3 Wireless Access Points (WAP)
- You lot can send data directly between 2 devices using WiFi provided that the devices have compatible wireless NICs fitted. This is very useful if you wish create a temporary connection between the devices, simply it can bear witness difficult to manage as you try to connect more devices.
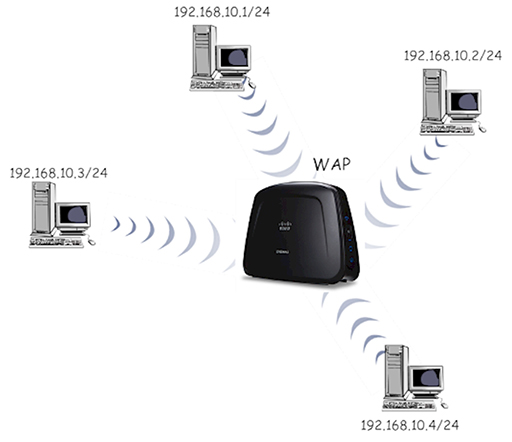
- Using a wireless access point in your network provides a central WiFi connection signal to which all WiFi capable devices must connect in order to exchange information. In effect, you accept created a star topology without wires:
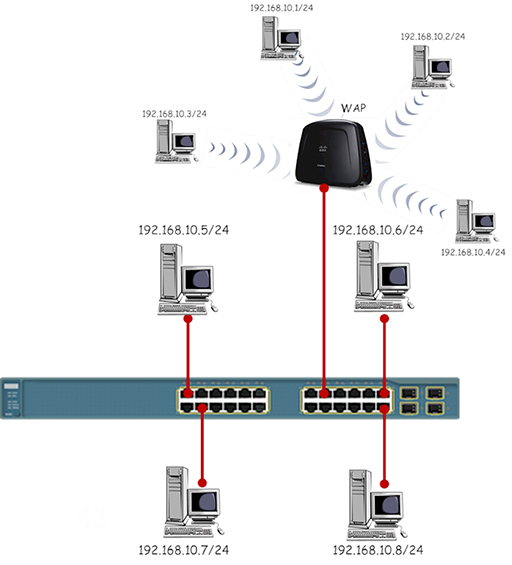
- While a single star topology WiFi network can be useful, y'all are more likely to meet WAPs connected to Ethernet switches, allowing the network to provide both wired and wireless network access:
eight Network address translation
- You volition have read about NAT when exploring IP package forwarding, only it is covered in more detail here.
- If you examine the diagram beneath, you volition see that the home LAN is using IP addresses in IP network 192.168.0.0/24, which will be the case for all the Isp's customers who are using the aforementioned blazon of home router. This will crusade issues, as the source and destination addresses take to be unique in every communication unicast (sending packets betwixt two devices).
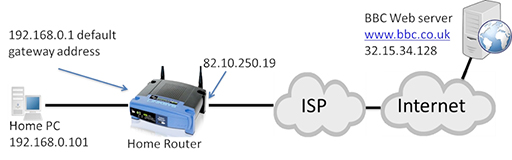
- Why practice home routers use the same accost on the abode LAN if it volition cause problems within the Internet? Recollect, IPv4 cannot provide sufficient IP addresses for all the devices that want to use IP, and so certain ranges of IP address, including 192.168.0.0/16, are set aside as private addresses.
- Private IP addresses can be used by anyone, at whatsoever time, within a private network. This addresses the consequence of non having sufficient IP addresses, just creates a trouble in that the IP address cannot be used to communicate over the Net as it is not unique. However, you lot will have a unique, public IP address assigned to your home router on the interface that connects to the ISP, which in the diagram higher up is 82.10.250.nineteen.
- The idea of NAT is to convert the source address from all outgoing LAN packets into the unique public accost assigned to the dwelling house router, and vice versa for incoming packets from the Cyberspace.
IP addresses in packets
- The image beneath shows a packet transmitted from the domicile PC towards the spider web server, which needs to be routed towards the Internet by the home router:
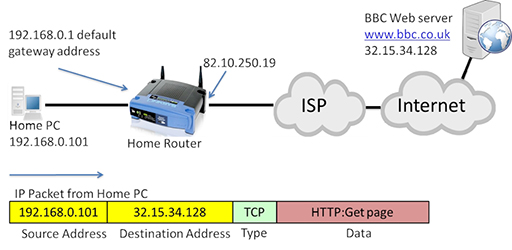
- Annotation that in the diagram above the source address is 192.168.0.101, which is individual.
- The packet will be received by the home router, which volition perform NAT, converting the source address to its own WAN interface IP address (82.10.250.19):
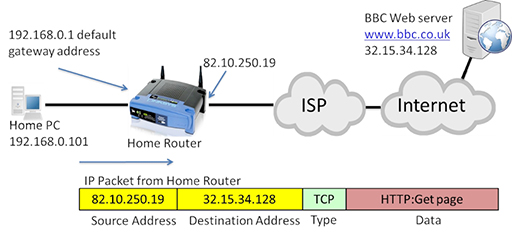
- The package tin now be forwarded through the Net to the destination web server, which will return the requested webpage in a series of packets:
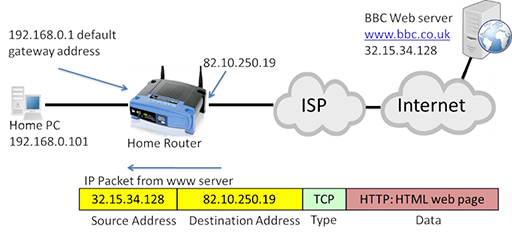
- The IP package is at present addressed with the web server interim as the source, and the public address of the home router WAN interface as the destination. The home router will accept the incoming packet, and translate the destination address back to the private IP address of the home PC:
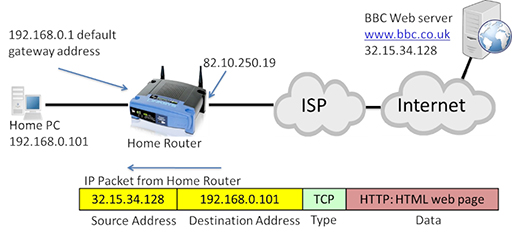
- The utilise of NAT and individual IP addresses has extended the life of IPv4 well across what would have been possible with the original range of addresses it provided. Private IP addresses and NAT are implemented inside well-nigh habitation and business concern networks.
9 Using networks securely
- You need to consider the security of your habitation network in order to protect your personal security. If your network is not secured, or you lot use information technology in an insecure way, so you increment the chance of threats to yourself and your data.
- Consider some of the activities that you undertake via the Internet:
- emailing
- sending photographs
- chatting
- posting to wiki
- shopping
- banking.
- What would be the impact if someone was able to intercept any information you lot sent while doing these activities? It could range from personal embarrassment to severe financial loss. Yous would probably not do whatsoever of these things with a stranger sat adjacent to you, but when y'all do them over the Internet, there is a run a risk that your data can exist intercepted past others.
- What could exist the motivation for trying to admission your data? The listing is long, but some popular reasons are:
- general nosiness
- a wish to dandy or get you into problem
- a wish to steal your money or data
- a want to impersonate you while carrying out a criminal activeness.
- To start securing your network, consider the passwords that you lot use to protect admission to your online accounts, and to your network devices such as PCs, tablets and home routers.
- Your passwords demand to be potent. Utilize a mix of numbers, messages and special characters. Practice non use annihilation that could be guessed, such equally a pet's proper noun or a birthday.
- Yous need to alter your passwords regularly in case other people learn them.
- Do non tell your passwords to anyone. Ever.
- If you take prepare a password hint, do not brand the hint too obvious.
- Do not use the aforementioned password across multiple accounts and devices. If someone learns information technology, they have access to everything.
- Practise not write your passwords downwards.
- Y'all likewise need to consider how your devices handle your passwords, as some volition try to exist helpful and store them for you. If you are using a public computer to access a website that requires yous to enter a password, the browser may offer to shop it for you. This is not a good thought, every bit the next user of the computer can access your passwords.
- If you log into your business relationship and and so walk off to do something else, leaving the figurer unattended, anyone else who is nowadays can access your account. If you leave your PC or device, logout from it first. Most PCs, tablets and smartphones can be configured to automatically logout after a brusk menstruum of inactivity, so observe out how to gear up this upwards.
12 Activities
Activity: Investigating your dwelling network
By signing in and enrolling on this course you can view and consummate all activities inside the course, track your progress in My OpenLearn Create. and when yous have completed a course, you lot tin can download and print a free Argument of Participation - which yous can use to demonstrate your learning.
Activity: Network devices and protocols – Package Tracer
We connect our devices to the Cyberspace and the Internet connects them all together. Only what is the Internet fabricated of? We say it interconnects all the devices, but how?
Network devices are mainly hubs, switches or routers. There are lots of other specialist bits, but the bulk of the interconnectivity is done by switches and routers. In this course you lot have looked at customer server models, spider web requests and emails. What do these letters look like and how are they sent?
For each type of communication over the network there are a set of rules and specifications as to what format and guild the information is sent. These are called protocols and they are central in understanding how the Internet works.
This Packet Tracer lab explores the devices and protocols used in figurer networks. You lot volition demand:
Activeness: Password hints
Companies practise not store a user'south passwords in clear text – they transport it through a scrambling algorithm to produce a 'hash', and the hash is then saved. The hash algorithm does not work in opposite, then you can't unscramble a hash to become the original countersign. When you lot enter your password the site uses the same algorithm to make a hash, which it then compares to the hash saved against your details.
Some sites allow you to shop password hints, and they save these equally clear text. Adobe was hacked in 2013, and its hashed passwords and hints were stolen for thousands of customers. The hackers looked at all the hints that gave the same hash (hence were the same password). Considering they had lots of hints for the same countersign it was easy to guess what they were.
Can you lot guess the passwords used in this puzzle based on the stolen hints?
13 Resource
For more information, take a look at the following resource.
- Sentinel this computer networking tutorial to explore what is a protocol:
Interactive feature non bachelor in unmarried page view (see information technology in standard view).
- For a detailed look at the complexity of what happens when you click a URL read Igor Ostrovsky'southward blog post.
- Read Google'southward guide to online safety.
- Read How-To Geek'southward guide to choosing a practiced password and sentinel the following video:
Interactive feature not available in single page view (come across it in standard view).
- Read Activity Fraud'south guide to phishing and watch the following video:
Interactive feature not bachelor in single page view (meet it in standard view).
- Watch this video on being cautious when using public WiFi:
Interactive characteristic not available in single page view (meet it in standard view).
14 Cease of course quiz
Now it's time to examination what y'all've learned in a quiz.
15 Acknowledgements
Grateful acknowledgement is made to the post-obit sources:
Effigy 1: Birmingham City University (BCU)
Figure 2: Birmingham City Academy (BCU)
Figure 3: Cisco
Figure 4: Birmingham City University (BCU)
Effigy 5: Birmingham City University (BCU)
Effigy half dozen: CommScope. This file is licensed nether the Creative Commons Attribution-Noncommercial-NoDerivatives Licence http://creativecommons.org/ licenses/ by-nc-nd/ 2.0/
Figure 7: tlsmith1000. This file is licensed under the Artistic Commons Attribution-Share Alike Licence http://creativecommons.org/ licenses/ past-sa/ two.0/
Figure 8: Bull3t Hughes. This file is licensed under the Artistic Eatables Attribution-Share Alike Licence http://creativecommons.org/ licenses/ by-sa/ 2.0/
Figure 9: Cisco
Figure 10: Cisco/Birmingham City University (BCU)
Effigy 11: Cisco/Birmingham City Academy (BCU)
Figure 12: Cisco/Birmingham Urban center University (BCU)
Figure thirteen: Cisco/Birmingham City University (BCU)
Effigy fourteen: Cisco/Birmingham City Academy (BCU)
Figure 15: Cisco
Figure xvi: Cisco/Birmingham City Academy (BCU)
Figure 17: Cisco/Birmingham Urban center University (BCU)
Figure 18: Cisco/Birmingham City University (BCU)
Figure 19: Publisher unknown
Effigy 20: Cisco/BCU
Effigy 21: Birmingham City Academy (BCU)
Figure 22: Birmingham City University (BCU)
Figure 23: Birmingham Urban center University (BCU)
Effigy 24: Birmingham Metropolis University (BCU)
Effigy 25: Birmingham City University (BCU)
Effigy 26: Publisher unknown
Figure 27: Screenshot taken from Barclays, example of phishing.
Every effort has been made to contact copyright holders. If any have been inadvertently overlooked the publishers will be pleased to make the necessary arrangements at the first opportunity.
Source: https://www.open.edu/openlearncreate/mod/oucontent/view.php?id=129583&printable=1
0 Response to "You Want to Know What Protocols Are Being Used on Your Network"
Post a Comment